Secure Collaboration
Enable seamless teamwork while maintaining enterprise-grade security across all your API projects. Our collaboration solutions provide protected environments for developers to work efficiently without compromising sensitive data. Advanced encryption and permission systems ensure only authorized personnel can access critical resources. Integration with private workspaces allows teams to collaborate while keeping proprietary information secure. Streamline your development process while meeting strict compliance requirements with our robust security framework.
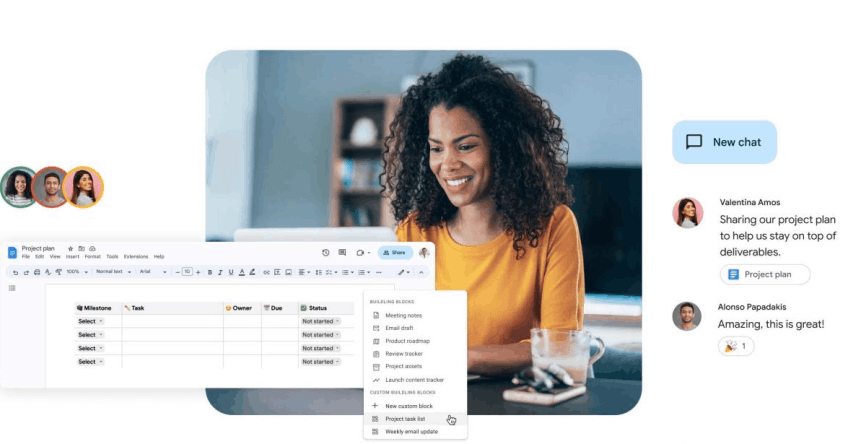
Team Workspaces
Create isolated private workspaces where your development teams can collaborate securely on API projects. Each workspace features encrypted communication channels and version-controlled documentation to maintain project integrity. Customizable permission levels ensure team members only access what they need for their specific roles. Real-time collaboration tools eliminate bottlenecks while audit logs provide complete visibility into all changes. Maintain productivity without sacrificing security in these fully configurable virtual work environments.

Cloud-Based Storage
Store and manage all your API assets in our highly secure cloud storage solution with military-grade encryption. Automated backups and version history protect against data loss while maintaining compliance with industry regulations. Our geographically distributed servers ensure 99.99% uptime and fast access from anywhere in the world. Advanced search capabilities and metadata tagging make it easy to organize and retrieve even complex API documentation. Scale storage seamlessly as your projects grow without worrying about infrastructure limitations.